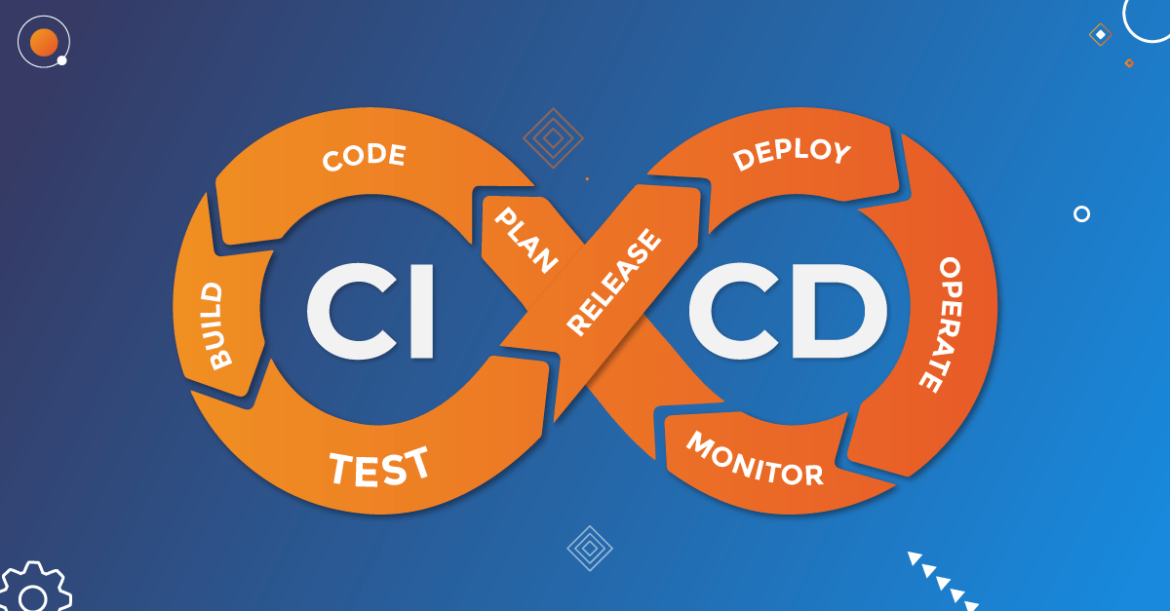
CI/CD stands for Continuous Integration and Continuous Deployment (or Continuous Delivery). It is a set of practices and methodologies that enable software development teams to deliver code changes more frequently, reliably, and efficiently.
Here’s a breakdown of each component:
- Continuous Integration (CI): CI focuses on merging code changes from multiple developers into a shared mainline frequently and automatically. With CI, developers integrate their changes into a central repository multiple times a day. This ensures that conflicts and issues are identified early, promoting collaboration and reducing the risk of integration problems. CI often involves automated build processes, code quality checks, and running tests to validate the changes.
- Continuous Deployment (CD) or Continuous Delivery (CD): CD extends CI by automating the process of deploying the integrated and validated code changes to production or other target environments. Continuous Deployment involves automatically releasing the software changes into production as soon as they pass the necessary tests and quality checks. Continuous Delivery, on the other hand, automates the release process but leaves the decision of when to deploy to production in the hands of the development team.
The primary goals of CI/CD are to:
- Increase Development Velocity: By automating build, integration, testing, and deployment processes, CI/CD reduces manual effort and allows developers to release code changes more frequently. This enables faster feedback loops, rapid bug fixes, and shorter development cycles.
- Improve Code Quality: Frequent integration and automated testing help catch integration issues, bugs, and regressions early in the development process. This leads to improved code quality, reduced technical debt, and more stable software.
- Enhance Collaboration: CI/CD encourages collaboration among developers, as they frequently integrate their changes and resolve conflicts. It also facilitates collaboration between developers, testers, and operations teams by automating processes and providing a shared understanding of the software delivery pipeline.
- Enable Rapid and Reliable Deployments: Automation in CI/CD streamlines the deployment process, reducing human errors and ensuring consistent and repeatable deployments. This helps to minimize downtime and allows for faster feature releases and bug fixes.
CI/CD is typically supported by various tools and technologies, such as version control systems (e.g., Git), build servers (e.g., Jenkins, Travis CI), containerization platforms (e.g., Docker), configuration management (e.g., Ansible, Puppet), and deployment orchestration (e.g., Kubernetes).
By adopting CI/CD practices, development teams can improve their development and delivery processes, accelerate software releases, and achieve higher levels of efficiency, quality, and agility.
Top 10 CI/CD Security Risks
Presented below are the top 10 CI/CD security risks. All risks follow a consistent structure –
Definition – Concise definition of the nature of the risk.
Description – Detailed explanation of the context and the adversary motivation.
Impact – Detail around the potential impact the realization of the risk can have on an organization.
Recommendations – A set of measures and controls recommended for optimizing an organization’s CI/CD posture in relation to the risk in question.
References – A list of real world examples and precedents in which the risk in question was exploited.
List of the top 10 CI/CD security risks:
CICD-SEC-1: Insufficient Flow Control Mechanisms
CICD-SEC-2: Inadequate Identity and Access Management
CICD-SEC-3: Dependency Chain Abuse
CICD-SEC-4: Poisoned Pipeline Execution (PPE)
CICD-SEC-5: Insufficient PBAC (Pipeline-Based Access Controls)
CICD-SEC-6: Insufficient Credential Hygiene
CICD-SEC-7: Insecure System Configuration
CICD-SEC-8: Ungoverned Usage of 3rd Party Services
Reference: https://github.com/cider-security-research/top-10-cicd-security-risks

Leave a Reply