-
MAC Flooding: Understanding the Attack
MAC flooding is a network attack that exploits the limitations of network switches by flooding the switch’s MAC address table. This attack aims to overload the table, causing the switch to operate in…
-
What is Sniffing ?
Network Sniffing: A Comprehensive Explanation Network sniffing refers to the practice of intercepting and inspecting data packets as they flow across a computer network. This process is often conducted for legitimate network monitoring…
-
What Is “Ping” and What it Does
Let’s delve into a detailed explanation of “ping.” Ping in Networking: A Comprehensive Overview Definition: “Ping” is a computer network diagnostic tool used to test the reachability of a host (typically a computer…
-
Find Device or IP Address using MAC Address
To find the device or IP address associated with a MAC (Media Access Control) address, you can use several methods depending on your network setup and tools available. Here are a few common…
-
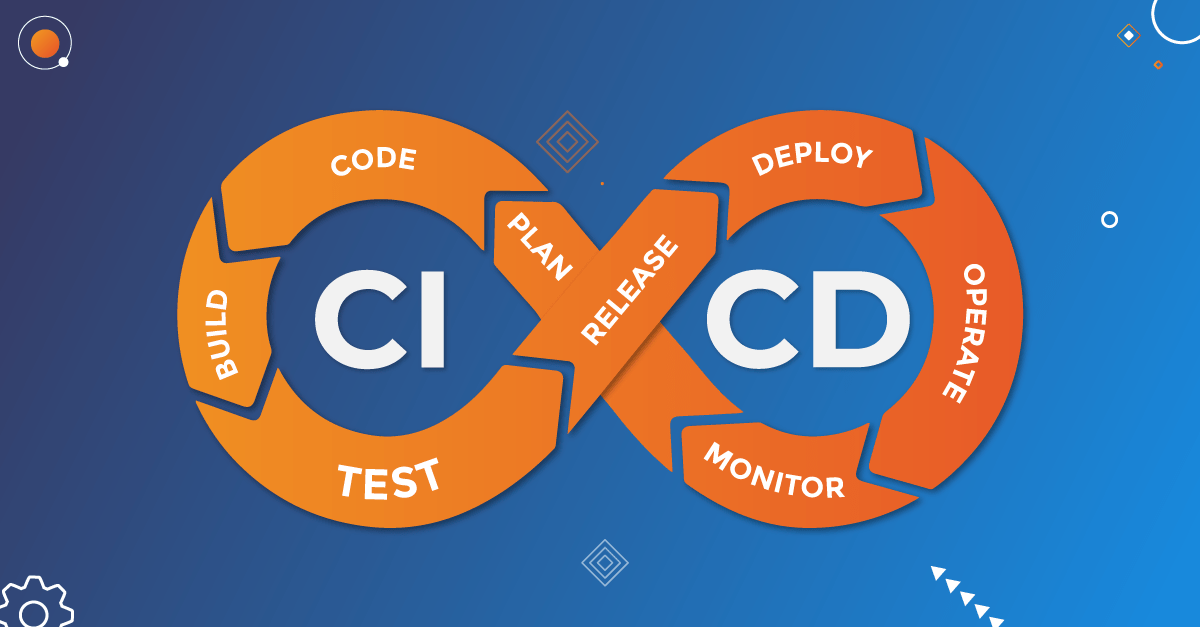
What is CI/CD and it’s Top 10 Risks
CI/CD stands for Continuous Integration and Continuous Deployment (or Continuous Delivery). It is a set of practices and methodologies that enable software development teams to deliver code changes more frequently, reliably, and efficiently.…
-
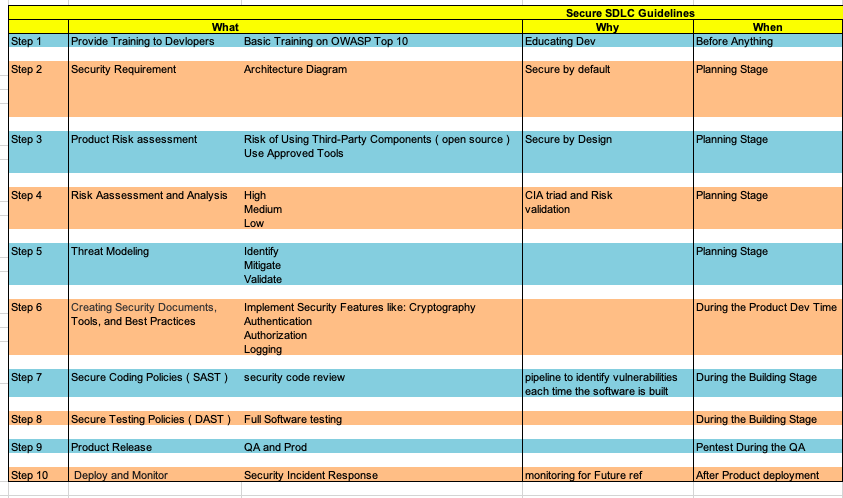
Secure SDLC
It has always has been the way, when we think of Security after we have been Compromised. Then why not think of Security during the building phase of an application. This is where…