Transport Layer Security/ Secure Socket Layer. It works at the application layer which provide a standard security technology for authentication and establishing a secure session using certificates.
How TLS Handshake Works:
Step 1) Client Hello
Step 2) Server Hello
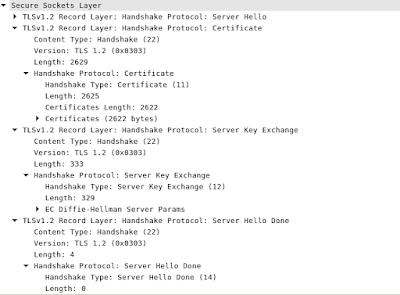
Step 3) Server send message to the client contains Certificates, Server encryption Key, and lastly Server Hello Done.
Step 4) Client responds to the server with encryption key, change cipher spec and Finished Message which contain the integrity check aka SHA Algo.
Step 5) Server sends Change cipher suits and the finished message which contain the integrity check.
How does it actually looks like! We will wireshark for analysis:
Client Hello:
 |
Server Hello:
Server Hello Done:
Client Finished Message:
Server Finished Message:
TLS encryption is done by 3 steps: Key Exchange, Data Encryption and Handshake Integrity.
Key exchange: Is a method where cryptographic keys are exchange between 2 systems, using a crypt algo like RSA, DH, ECDH.
Data Encryption: In TLS it’s called as Ciphers. Eg., 3DES, AES algo(s).
Handshake Integrity: Uses SHA algorithm to provide integrity.
How public and private keys are exchange:
Step 1) Https client connect with the https sever
Step 2) Https server sends a certificate which contains 2 large prime numbers aka Public Keys.
Step 3) Https client choose a Private Key, generate Encryption key using Public Keys sent by https server.
Step 4) Server generate encryption key based on it’s private key.
Now both share the same shared key.
Step 5) Now both send encrypted message with their shared secret key.
Certificate Chain:
1) First we need Certificate Authority Server (CA)
2) CA will generate a Root Certificate
3) Root Certificate will generate a Intermediate Certificate
4) We sign that Intermediate Certificate Which matched with the Root Certificate
5) After signed Certificate it will issue a Server Certificate, which contains the Domain name.
6) That Intermediate Certificate in uses by the browser.
When we type “Google.com” in the search bar of the browser and hit enter,
1) Server Sends a Certificate to the browser,
2) Browser will verifies the server certificate issues by the Intermediate Certificate
3) It will then checks whether it contains the “Google.com” domain name or not
4) If matches, it’s a secure connection,
5) It it doesn’t matches, then connection is not secure. There can be many reasons for error. Like: Expiration of Certificate or Invalid certificate.
Bad TLS Encryption Examples:
1) Browser using TLS version less then 1.2
2) Using 3DES algorithm
For Safe Encryption Examples:
1) TLS version more then 1.2
2) Using ECDHE key exchange algorithm
3) Using AES algo.
4) For message integrity using SHA algo, e.g., SHA1.





Leave a Reply