Simple Network Management Protocol, works at the Application layer, uses UDP as a transport protocol to manage or monitor hardware and software in a IP network.
It collect and organize information of the network devices like modem, routers, switches, servers used and able to modify them if needed.
How it work:
1) SNMP Request via snmp manager (A and B)
This is how it looks in wireshark;
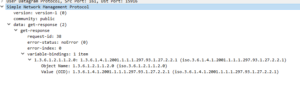
2) SNMP Response via snmp agent
This is how it looks in wireshark;
SNMP Manager:
It is an management system or console, which sends IP related query information to the SNMP agent to manage or to make any configuration.
SNMP Agent:
It monitors any system or any network device and responds to the query back to the SNMP manager. It can also send error messages to the SNMP manager if any illegal access has occur.
Step 1) SNMP manager, Host A send a request to another system, Host B.
Step 2) SNMP manager will create a SNMP message which will contain the number of active sessions, community of SNMP manager, destination (Host B) IP address.
Step 3) SNMP server will then send this message to the Host B.
Step 4) Host B will then receive the requested message.
Step 5) Host B will then verifies or monitor the message, comparing the community of SNMP manager and Source IP address for access permission.
Step 6) If requested content does not match or if it does not have access permission, SNMP agent will send an request of Authentication Error to the community of SNMP manager. And then Community will response to the SNMP agent.
Step 7) In response, Community give the session information of that request to the SNMP agent.
Step 8) SNMP manager will then retrieve that message which contain the IP address of the source Host A back to Destination to Host B.
Step 9) Host B will now response back to the Host A of it’s request. Now both the Hosts will communicate.
Use of SNMP:
It is used to reset passwords remotely.
We can re-configure IP addresses.
We can collect error reports, into a log and also send alerts on error condition.
We can also send alerts for device failure or shortage in Memory use or CPU usage.
We can collect information about how much bandwidth is being used.



Leave a Reply