What is XZ Utils, and what is the XZ backdoor?
XZ Utils and its underlying library liblzma is a free software tool that implements both XZ and LZMA, which are two compression/decompression algorithms widely used in Unix-based systems, including Linux systems. XZ Utils is used by many operations on those systems for compressing and decompressing data.
The CVE-2024-3094 backdoor found in XZ Utils was implemented to interfere with authentication in SSHD, the OpenSSH server software that handles SSH connections. The backdoor enabled an attacker to execute remote code via an SSH login certificate. Only XZ Utils versions 5.6.0 and 5.6.1 are impacted.
What is the XZ Backdoor’s Impact:
The objective of the backdoor was evident: unauthorized remote access. By compromising RSA public key validation within sshd, attackers could circumvent authentication and execute arbitrary commands. Picture an entire server exposed, susceptible to the whims of the attacker.
The potential grave repercussions:
Data Leakage: Valuable information such as customer data, intellectual property, and financial records could be illicitly extracted.
System Hijacking: Attackers could attain total system control, deploying malware, disrupting operations, or initiating subsequent attacks.
Horizontal Progression: The compromised system could serve as a launching pad for attackers to traverse within the network, aiming at other vital systems.
Are you impacted, How to check:
We can perform the following commands in our terminal:
cmd> apt-cache policy liblzma5
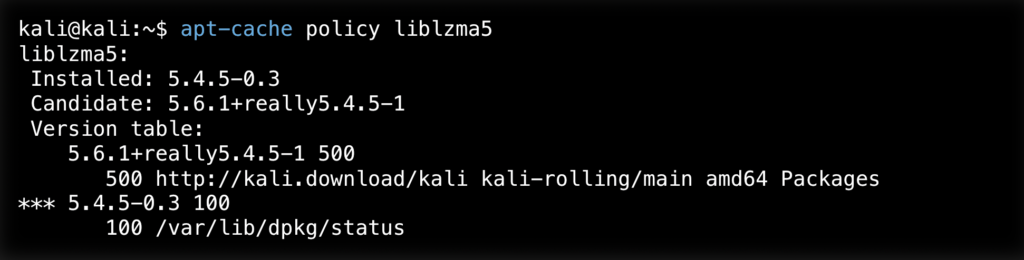
In Kali:
If we see the version 5.6.0-0.2 next to Installed: then we must upgrade to the latest version, 5.6.1+really5.4.5-1.
We can do this with the following commands: sudo apt update && sudo apt install -y –only-upgrade liblzma5

XZ backdoor: A highly technical attack
In addition to the highly elaborated social engineering the backdoor itself is very complex.
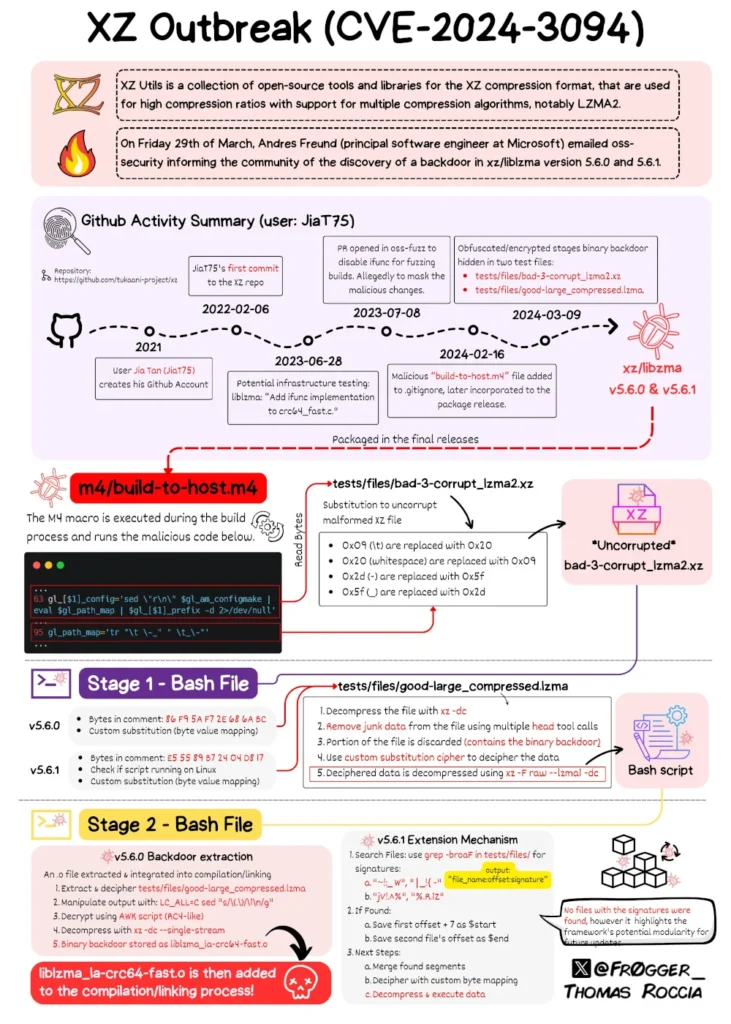
Microsoft’s senior threat researcher Thomas Roccia designed and published an infographic to show the whole operation leading to CVE-2024-3094. As shown in the below XZ Outbreak.
The backdoor is composed of several parts that have been included over multiple commits on the XZ Utils GitHub, described in depth by Freund.
Which operating systems are impacted by the XZ backdoor?
Thanks to Freund’s discovery, the attack was stopped before being spread on a wider scale. The cybersecurity company Tenable exposed the following operating systems known to be affected by the XZ backdoor:
- Fedora Rawhide.
- Fedora 40 Beta.
- Fedora 41.
- Debian testing, unstable and experimental distributions versions 5.5.1alpha-01 to 5.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- Kali Linux.
- Arch Linux.
A Near Miss: Thankfully, Not a Wide-Ranging Catastrophe
Fortunately, the backdoored versions (5.6.0 and 5.6.1) were still relatively new and hadn’t been incorporated into stable releases of most Linux distributions. Prompt detection by security researcher Andres Freund averted a widespread compromise.
How to mitigate and protect from this XZ backdoor threat:
More systems might be affected, especially those on which developers compiled the vulnerable versions of XZ. Security company Binarly offers an online detection tool that could be used to test systems to see if they are affected by the XZ backdoor.The version of XZ should be carefully checked, as versions 5.6.0 and 5.6.1 contain the backdoor. It is advised to revert to a previous known safe version of XZ Utils, such as 5.4.
How to mitigate and protect from this XZ backdoor threat:
More systems might be affected, especially those on which developers compiled the vulnerable versions of XZ. The version of XZ should be carefully checked, as versions 5.6.0 and 5.6.1 contain the backdoor. It is advised to revert to a previous known safe version of XZ Utils, such as 5.4.
Mitigation Strategies:
- Strengthening Our Defenses: While the immediate threat has been addressed, here’s how you can mitigate future risks:
- Identify Vulnerable Systems: Check your package manager for installed XZ Utils versions. Versions 5.6.0 and 5.6.1 pose potential vulnerabilities.
- Patch Promptly: Apply the latest patches provided by your Linux distribution provider. Consider downgrading to a secure version (typically predating 5.6.0).
- Enhance SSH Security: Explore additional security measures such as multi-factor authentication (MFA) and restricting SSH access to specific IP addresses or usernames.
- Monitor for Suspicious Activity: Maintain vigilance and monitor logs for any abnormal activities suggestive of compromise.
Lessons Learned:
This incident serves as a stark reminder of the persistent risks associated with open-source software. While collaboration fosters innovation, it also presents opportunities for malicious actors. Here are some key takeaways:
- Scrutinize Code Contributions: Maintaining a healthy skepticism towards new contributors, particularly those exhibiting sudden bursts of activity, is essential.
- Embrace Automated Code Reviews: Leveraging automated tools to scan code for vulnerabilities can serve as a valuable initial defense.
- Stay Updated: Timely patching of systems is crucial. Don’t leave outdated software vulnerable to exploitation.
Software supply chain attacks are increasing…
Supply chain attacks are increasingly being used by threat actors. Yet usual software supply chain attacks mostly consist of managing to compromise a key account in the process of the development of software, and use the account to push malicious content to legitimate software, which often gets detected quite rapidly. In the XZ Utils case, it is very different because the threat actor carefully managed to gain the trust of legitimate developers and become one of the maintainers of the tool, allowing him to slowly push different vulnerable parts of code into the software without being noticed.
Software supply chain attacks are not the only increasing threats; other supply chain attacks based on IT products are also increasing.
Therefore, companies should ensure that third parties are taken into consideration in their attack surface monitoring.
The Road Ahead:
The open-source community bears the responsibility of remaining vigilant. It’s imperative to implement stricter code review processes and utilize continuous integration/continuous delivery (CI/CD) pipelines with integrated security checks. This incident underscores the vulnerability of even the most trusted tools. Through collective efforts, we can pave the way towards a more secure open-source future.
Little History on XZ Backdoor.
On March 29, 2024, Microsoft software engineer Andres Freund reported the discovery of the backdoor. He found it when he became interested in odd behavior of a Debian sid installation, such as SSH logins taking a lot of CPU and Valgrind errors and decided to analyze the symptoms in depth. Freund explained that the discovery of the backdoor in XZ was luck, as it “really required a lot of coincidences.”
Yet it appears that the implementation of the backdoor has been a very quiet process that took about two years. In 2021, a developer named Jian Tan, username JiaT75, appeared out of the blue to start working on the XZ Utils code, which is not unusual because developers of free software often work together on updating code. Tan contributed frequently to the XZ project since late 2021, slowly building trust in the community.
In May 2022, an unknown user using the fake name Dennis Ens complained on the XZ mailing list that the software update was not satisfying. Another unknown user, Jigar Kumar, came into the discussion two times to pressure the main developer of XZ Utils, Lasse Collin, to add a maintainer to the project. “Progress will not happen until there is new maintainer,” Jigar Kumar wrote. “Why wait until 5.4.0 to change maintainer? Why delay what your repo needs?”
Meanwhile, Collin expressed that “Jia Tan has helped me off-list with XZ Utils and he might have a bigger role in the future at least with XZ Utils. It’s clear that my resources are too limited (thus the many emails waiting for replies) so something has to change in the long term.” (Collin wrote Jia in his message while other messages reference Jian. To add to the confusion, Jian’s nickname is JiaT75.)
In the months that followed, Tan became increasingly involved in XZ Utils and became co-maintainer of the project. In February 2024, Tan issued commits for versions 5.6.0 and 5.6.1 of XZ Utils, both of which contained the backdoor.
It is also interesting to note that in July 2023, Tan requested to disable ifunc (GNU indirect function) on oss-fuzz, a public tool made to detect software vulnerabilities. That operation was probably done to allow the backdoor in XZ to stay undetected once it was released, as the backdoor makes use of that function to achieve its goals.
Finally, several persons responsible for different Linux distributions have been contacted by the attacker to include the backdoored versions of XZ Utils in their own distributions. Richard WM Jones from RedHat wrote about it on a forum: “Very annoying – the apparent author of the backdoor was in communication with me over several weeks trying to get xz 5.6.x added to Fedora 40 & 41 because of it’s ‘great new features’. We even worked with him to fix the valgrind issue (which it turns out now was caused by the backdoor he had added). We had to race last night to fix the problem after an inadvertent break of the embargo. He has been part of the xz project for 2 years, adding all sorts of binary test files, and to be honest with this level of sophistication I would be suspicious of even older versions of xz until proven otherwise”. Tan also tried to have it included in Ubuntu.


Leave a Reply