Secure SDLC
It has always has been the way, when we think of Security after we have been Compromised. Then why not think of Security during the building phase of an application.
This is where DevSecOps comes in where Secure Software Development Life Cycle (SDLC) takes place.
It is a process in the design which consists of Training, Risk analysis, code scanning, penetration testing and vulnerability management.
Below are the steps which requires a walk though during the time of Development and also in post development.
( Steps can be shorten and added depending upon the requirement. )
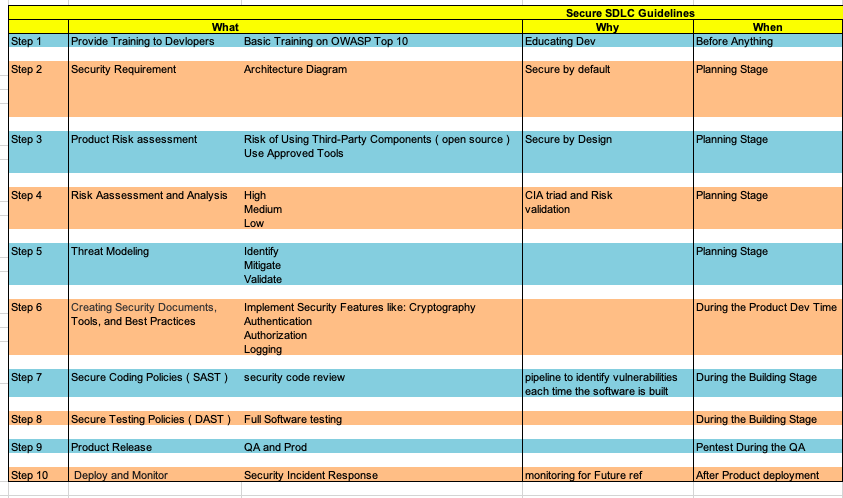
This tells us the What, When and Why of the Secure SDLC.
Step 1: Provide Training to the Developers
What: Basic training of Web application Security, like OWASP Top 10, Network protocols, Attack vectors, encryption, CIA Triad
When: Before any development
Why: Because, it gives Developer an perspective of the attack which can happen due to poor coding and weak logic
How: OWASP Top 10, CIA Triad, Networking protocols.
Step 2: Design Requirement
What: This gives an big picture of the application which is to be build.
When: During the the time of development. ( Planning Stage)
Why: This will help us in placing the security tools accordingly.
How: Approved Libraries and Cryptography, Input Sanitization, MFA.
Step 3: Product Risk Assessment
What: Analysis of the 3rd party and open source tools before using them
When: During the Network architecture. ( Planning Stage)
Why: To have the control over the tool used according to the application functionality.
How: Project dependencies, vulnerability fixes or patching
Step 4: Risk Analysis
What: To follow the CIA triad and to risk validation.
When: During the Planning Stage
Why: To help us with the Risk and give us an compliant application.
How: Mitigate the high risk as soon as possible. DeAnonymization, Data Breach, Data loss, Data corruption.
Step 5: Threat Modeling
What: It is to analyse the Risk calculate in depth for the Risk assessment and
When: During the planning Stage of Development.
Why: To have an early mitigation and validation of the any identifies threat.
How: Mitigate the Identified threat as soon a s possible and do a validation post mitigation.
Step 6: Documentation
What: Creating Security Documents, tools used and the best practices.
When: During the product development time.
Why: To address the process, milestone,
How: Have a wiki page of bus found and mitigation.
Step 7: Static Application Security Testing
What: Code scanning using the tools for any bug or logical error.
When: During the building stage
Why: So that, we can fix the bugs at the earliest and minimize the false positives Integrate in the CI/CD pipeline so that, we can be notified each time code changes, or new build.
How: SonarQube, Snyk, Veracode, and more. ( Choose as per the application requirement)
Step 8: Dynamic application Security Testing
What: It is to test the application outside of the dev like any attacker will do.
When: When the application is running and code is not available to the the tester.
Why: As it interact with the application from the outside and useful to the company compliant standards
How: Nikto, OWASP ZAP ( Choose as per the application requirement)
Step 9: Product Release, QA
What: It is similar to the DAST but, it involves with other factors like, OS vulnerabilities, Hardware configurations, and social engineering.
When: Generally company outsourced the testing if they don’t comprise the in-house resources. In order to find the vulnerabilities in firewalls, servers, open ports, routers.
Why: Breaking things before a Hacker do.
How: Burp proxy, Nessus
Step 10: Deploy and Monitor
What: It is to collect the logs and send them to the SIEM system is useful to detect any abnormalities and live attack which can be prevented and alerted.
When: After the product has been deployed in the endpoint(s).
Why: It gives us the 24*7 window to the malicious activities and that which can be carried out by Incident response team.
How: Involve Incident Response team for integrating the application with the SIEM solution.
Ref :
https://github.com/tanprathan/OWASP-Testing-Checklist
https://owasp.org/www-project-web-security-testing-guide/assets/archive/OWASP_Web_Application_Penetration_Checklist_v1_1.pdf
https://www.sans.org/reading-room/whitepapers/bestprac/paper/36872
https://cheatsheetseries.owasp.org/IndexASVS.html