Firewall
-
Bypassing AV – Avast, on a Windows 7
Bypassing Avast Antivirus: A Hands-On Guide In today’s cybersecurity landscape, bypassing antivirus (AV) software is a critical skill for penetration testers and malicious actors alike. In this lab, we’ll explore how to bypass…
-
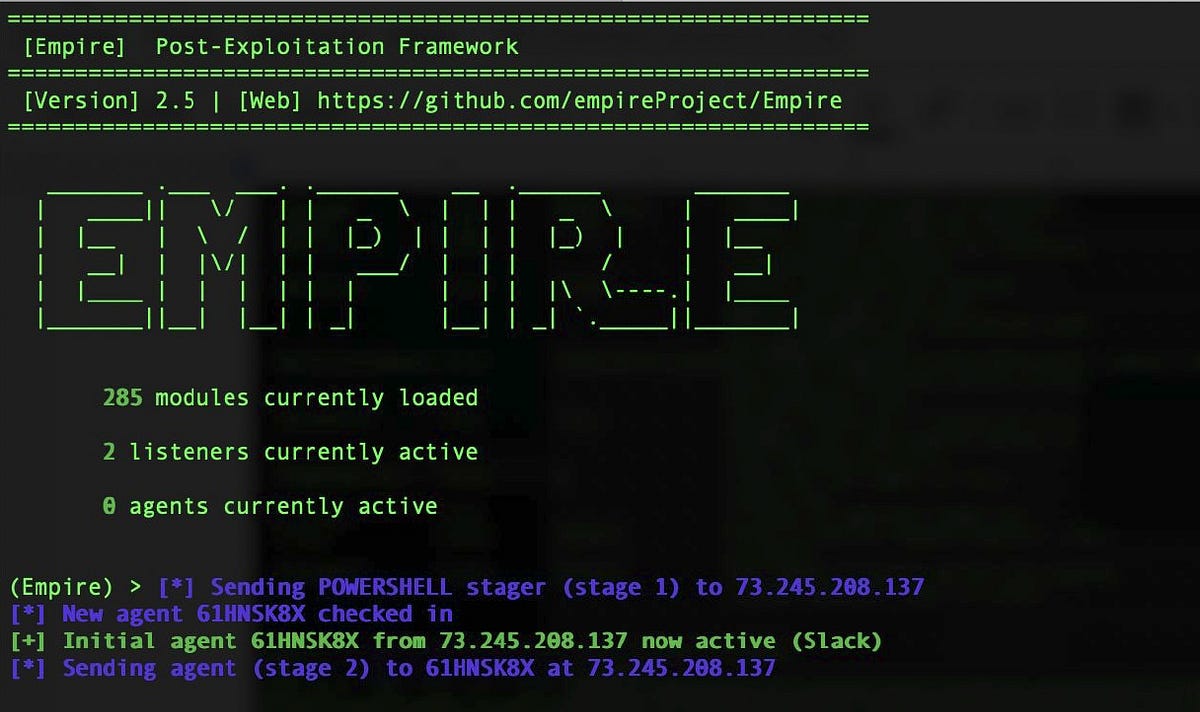
Leveraging PowerShell During Exploitation – Empire
Using Empire is another powerful approach for attackers looking to leverage PowerShell for exploitation and maintaining control over compromised systems. Empire is a post-exploitation framework that facilitates various attack vectors and includes modules…
-
Leveraging PowerShell During Exploitation
Leveraging PowerShell during exploitation is a common technique used by attackers due to its powerful capabilities and its presence on most Windows systems. Here are several methods and techniques for using PowerShell during…
-
Understanding Same Origin Policy (SOP) and Cookies: A Practical Lab Guide
In today’s interconnected web landscape, security measures like Same Origin Policy (SOP) and cookie management play pivotal roles in safeguarding user data and ensuring secure interactions between web applications. This lab guide provides…
-
Web Application Attacks
Here are some common web application attacks, each explained with examples: 1. SQL Injection Description: Attacker inserts or manipulates SQL queries to execute arbitrary commands on the database. Example:Input: ' OR '1'='1Query: SELECT…
-
Review Webserver Metafiles for Information Leakage
Reviewing web server metafiles for information leakage is a crucial aspect of web security. Metafiles such as robots.txt, .htaccess, and server configuration files can inadvertently expose sensitive information that could be exploited by…