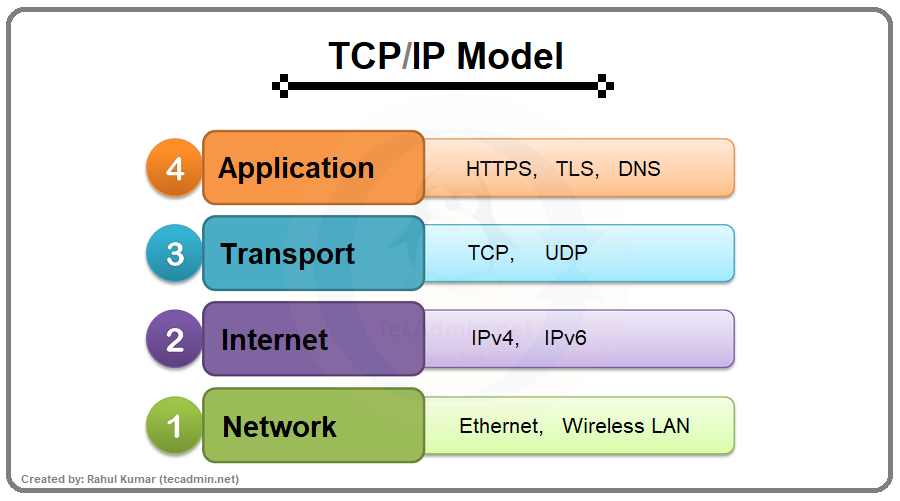
TCP/IP Model
TCP/IP is a language or set of rules a system use in order to access the internet. It provide end-to-end connectivity depending upon the message specification like format, addressing, routing with respect to the receiving end.
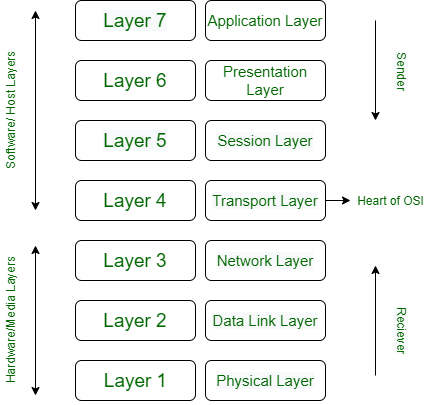
TCP/IP Model:
1)Application Layer
2)Transport Layer
3)Internet Layer
4) Network Access Layer
Application Layer:
This layer is the combination of Session, Presentation and Application layer of OSI Model. It provide user services for exchanging application messages or data communication. HTTP is a protocol that was designed for transmitting messages back and forth between a web client or browser to a web server. Telnet, it’s a protocol/client/server which allow to do TCP connection to any port that we specifies. FTP, is a clear text, a protocol without encryption, it gives us ability to send message back and forth between unix,. we can send message from sender to recipent using SMTP protocol.
Some of the Protocols it use: HTTP, FTP, SMTP, DHCP, POP, TLS/SSL, Telnet
Example:
This is what application Layer look like in wireshark, containing HTTP Header details.
Transport Layer:
It handle end-to-end delivery using TCP/ UDP. TCP handles connection oriented communications where it guarantees delivery of message and also make sure, somebody on the other end is their to receive it. UDP is connection less communication channel, where it just send the message but not really care about receiver side acknowledgement.
Internet Layer:
This is same as the Network layer of the OSI model. It provide processing rules, which ensure the data transmission. It does identification, addressing and routing . Protocols uses: IP, ICMP, IGMP.
Network Access Layer:
This layer is the combination of Physical and Data link layer of OSI Model also called as Link Layer. It handles all the physical connection, error correction and control of physical device. In this layer, we can transmit messages between hosts in a same network and also to other network using tunneling or VPN.
Example:
This is what Network Layer look like in wireshark.
*Groundwork:
Every piece of communication that goes across the internet is using the TCP/IP protocol suit. When we open a web application, it issue a series of TCP request in order to get all the content on that page to us. All these protocols are interconnected together. Generally, it issue an HTTP request, which gets encapsulated inside TCP which gets encapsulated inside IP, which again encapsulated inside an ethernet and then it sent across the communication channel wire or wireless, till it reach to another networking device and finally to the network provider.
TCP Flags:
We need Flags in order to identify or to analyse the network traffic in a more efficient way. Here the the 9 types of TCP flags and see how it looks in wireshark :
1) SYN
SYN or Synchronization flag is a first step in establishing a a TCP 3-way Hand-shake between the hosts.
2) ACK
ACK or Acknowledgement flag is used in acknowledging the successful receipt of the packet.
3) FIN
FIN or Finish flag, is generally send from the user side, saying no more data to be send aka last packet.
4) PSH
PSH or Push flag, is used to send data, telling it to process instead of buffering. Similar to URG but may have chances to get avoided or drop of packets.
5) URG
URG or Urgent packet is similar to PSH flag, but for the data to be send over wire with URG flag set, makes TCP to create a separate segment for it. So that, data won’t get drop.
6) RST
RST or Reset flag is used to send packet to a specific host, when that host is not accepting it.
7) ECE
ECE or Explicit Congestion Notification, is an option flag used in tcp connection to notify about the packet drop to both sides, sender as well as to receiver side.
8) CWR
CWR or Congestion Window Reduced is similar to ECE, used for notification purpose but it is used by sender only.
9) NS
NS or Nonce Sum is used to check and protect against the hidden malicious content in the packet send by sender. It is an experimental flag.