Cryptography
What is Cryptography ?
It is a process of providing security to the information and resources from unauthorized access.
Process includes converting data into encrypted data and then decrypt it into original data
Cryptography follow CIA Triad: Confidentiality Integrity Availability
Confidentiality: Protect information from 3rd party.
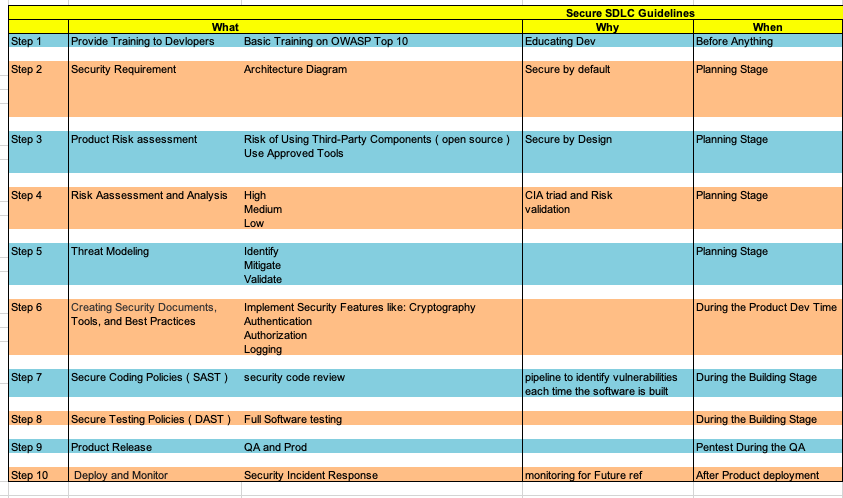
Integrity: Information should not be altered in any form.
Availability: To be available when called upon via authorized personage.
Why Cryptography?
It Makes Secure Web sites and Safe electronic transmission (Secure Key Exchange)
It Supports message authentication as well as encryption (Prevent us form MITM attack)
Types of Cryptography
Symmetric Cryptography:
It uses same keys to encrypt and decrypt data.
Process: Sender->data->key->cipher text->key->data->Receiver
Where both the sender and the receiver should know the secret key that is used to encrypt and decrypt the data.
Types of Symmetric Cryptography:
Stream Cipher:
Process: Sender -> plain text -> cipher -> send over -> Receiver
Algorithm uses: RC4
Block Cipher:
Process: Sender -> plain text -> Break text in blocks -> Encrypt 1st block ->Add the 1st block cipher to next 2nd block sequence -> to next block… till the last block -> send over -> Receiver
Algorithm uses: DES, 3DES, AES, Blowfish, Twofish
Symmetric Examples: Blowfish, Twofish, AES, RC-4,5,6, DES, 3DES
Algorithms: AES-128,192,256
Strength:
It is faster then Asymmetric and it is difficult to crack.
It does file encryption and files in storage using AES algorithm
It does VPN encryption uses AES256 algorithm.
Financial transaction security uses 3DES algorithm.
Weakness:
It needs individual keys for every other session for secure transmission.
It does not provide non-repudiation.
Lacks in message, website security and key transfer.
Asymmetric Cryptography:
It uses two different keys private and public key. For one to encrypt and other key to decrypt.
Process: Sender->data->Receiver’s-Public-key->cipher text->Private-key->data->Receiver
Asymmetric Examples: RSA DSA ECC
Algorithms:Diffie-Hellman, RSA, ECC, ElGamal, DSa
Strength:
It give us message encryption and authentication, which helps us from Men In The Middle Attack.
Website Security and digital signature.
Secure key exchange and management.
Weakness:
It is slower then Symmetric Key Exchange.
It works best along with Symmetric Key Cryptography.
Cryptography Python Examples:
Library Used: pycrypto
Python Version: Python 3.6.3
Message Length: Multiple of 16
Encryption Example:
#sample script for encrypting text
from Crypto.Cipher import AES
from Crypto.Cipher import AES
obj = AES.new(‘This is a key123’, AES.MODE_CBC, ‘This is an IV456’)
message = “May The Force Be With Us ”
#Encryption
ciphertext = obj.encrypt(message)
print(‘n’, ciphertext)
Output:
xb’lxacx18&xadvxa6x8ax9bZxfd}xf9xe6″x9ex9cX’N8gxe2xb5,!FxddJxe3xa7xab’
Decryption Example:
#sample Script for encryption and decryption
from Crypto.Cipher import AES
from Crypto.Cipher import AES
obj = AES.new(‘This is a key123’, AES.MODE_CBC, ‘This is an IV456’)
message = “May The Force Be With Us “
#Encryption
ciphertext = obj.encrypt(message)
print(‘n’, ciphertext, ‘n’)
obj2 = AES.new(‘This is a key123’, AES.MODE_CBC, ‘This is an IV456’)
#Decryption
result = obj2.decrypt(ciphertext)
print(result, ‘n’)
Output:
b’lxacx18&xadvxa6x8ax9bZxfd}xf9xe6″x9ex9cX’N8gxe2xb5,!FxddJxe3xa7xab’
b’May The Force Be With Us
Another Example of Both Encryption and Decryption:
#Sample Encryption and Decryption
from Crypto.Cipher import AES
obj = AES.new(‘This is a key123’, AES.MODE_CBC, ‘This is an IV456’)
message = “This is some text we need to encrypt because it’s very secret “
#Encryption
ciphertext = obj.encrypt(message)
print(‘n’, ciphertext, ‘n’)
obj2 = AES.new(‘This is a key123’, AES.MODE_CBC, ‘This is an IV456’)
#Decryption
result = obj2.decrypt(ciphertext)
print(result, ‘n’)
Output:
b’Gx0cxc9:xd2kxd7gxf0x9dxdaxb2xc0x10x1cx97Exb2xc4xcex9fxb6xd6x05Gx89xa1<xe6xd5{0xe7xe6xdd[xe8Pxdaxd8Px04xcfBxb2{vxb8x03x0fxb9xcexc3dxaa_xa0x99xefxe2xb54xdb\’
b”This is some text we need to encrypt because it’s very secret “